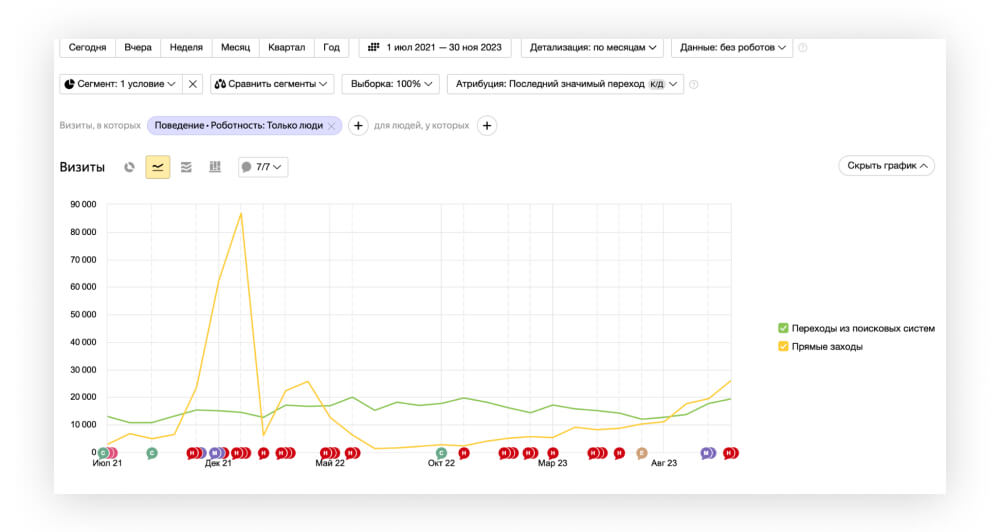
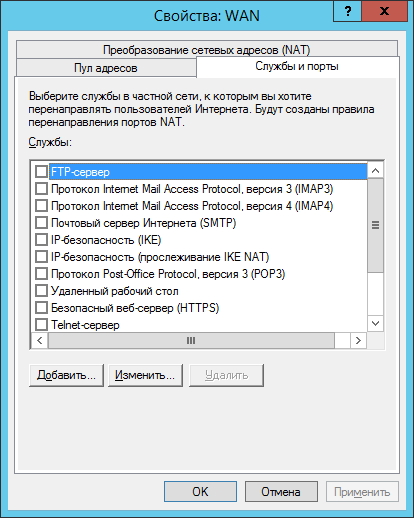
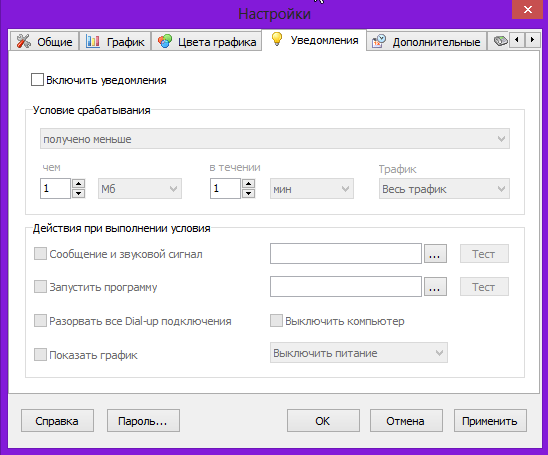
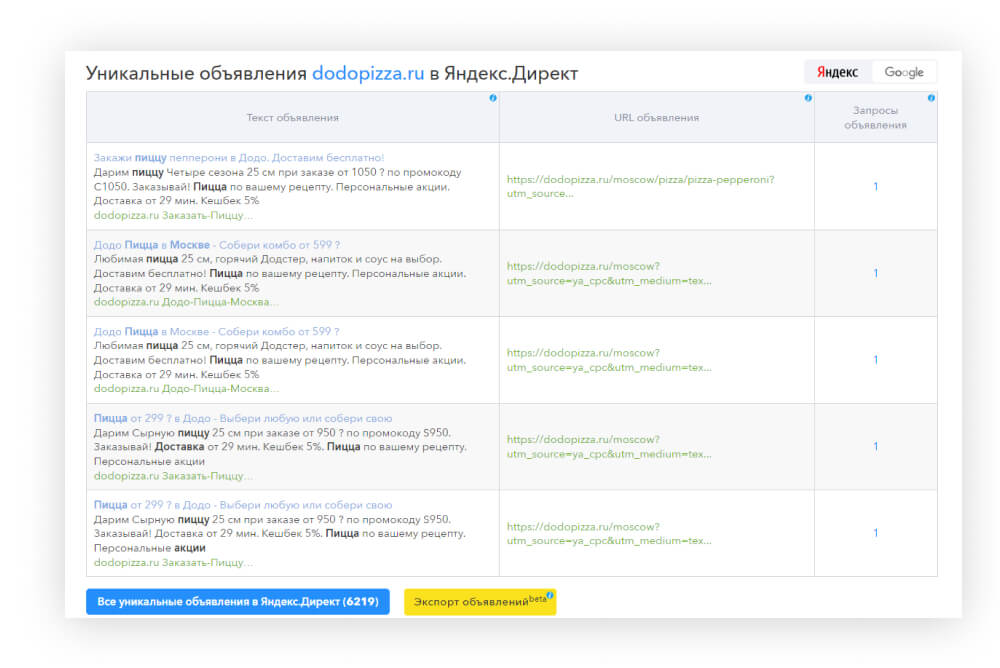
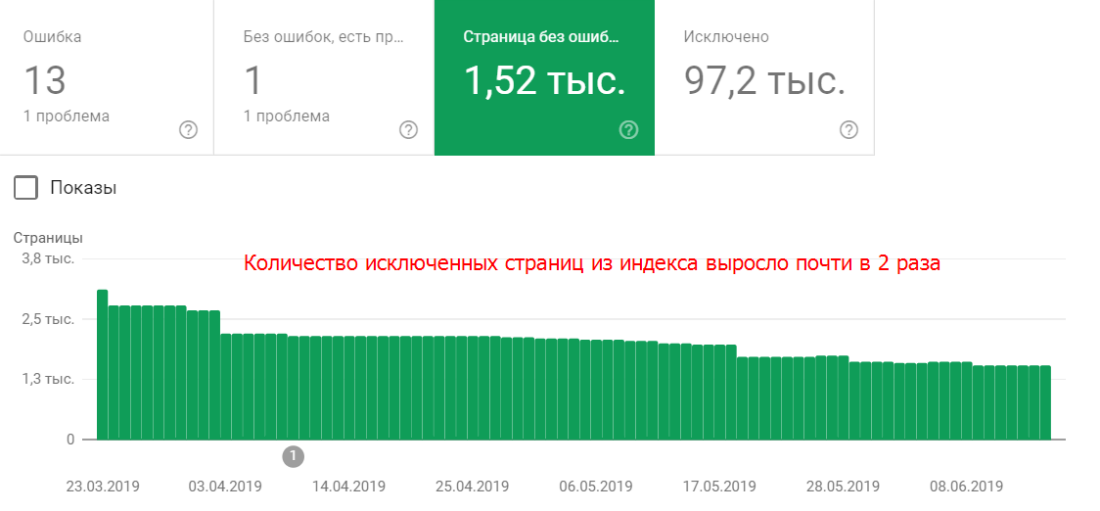
Anyplace control кончился трафик через интернет
VIEWS GALLERIES5
Download as PDF. Immediate printing plays a critical duty in conference limited task deadlines and dealing with unforeseen demands, making sure prompt implementation. In scenarios calling for immediate focus, immediate printing services come to be essential. Whether meeting limited target dates or dealing with unforeseen requirements, these solutions prioritize rapid shipment without jeopardizing on quality. Тема не простая но и не сложная ArataurNiladwyn gmail. Всем добрый день.
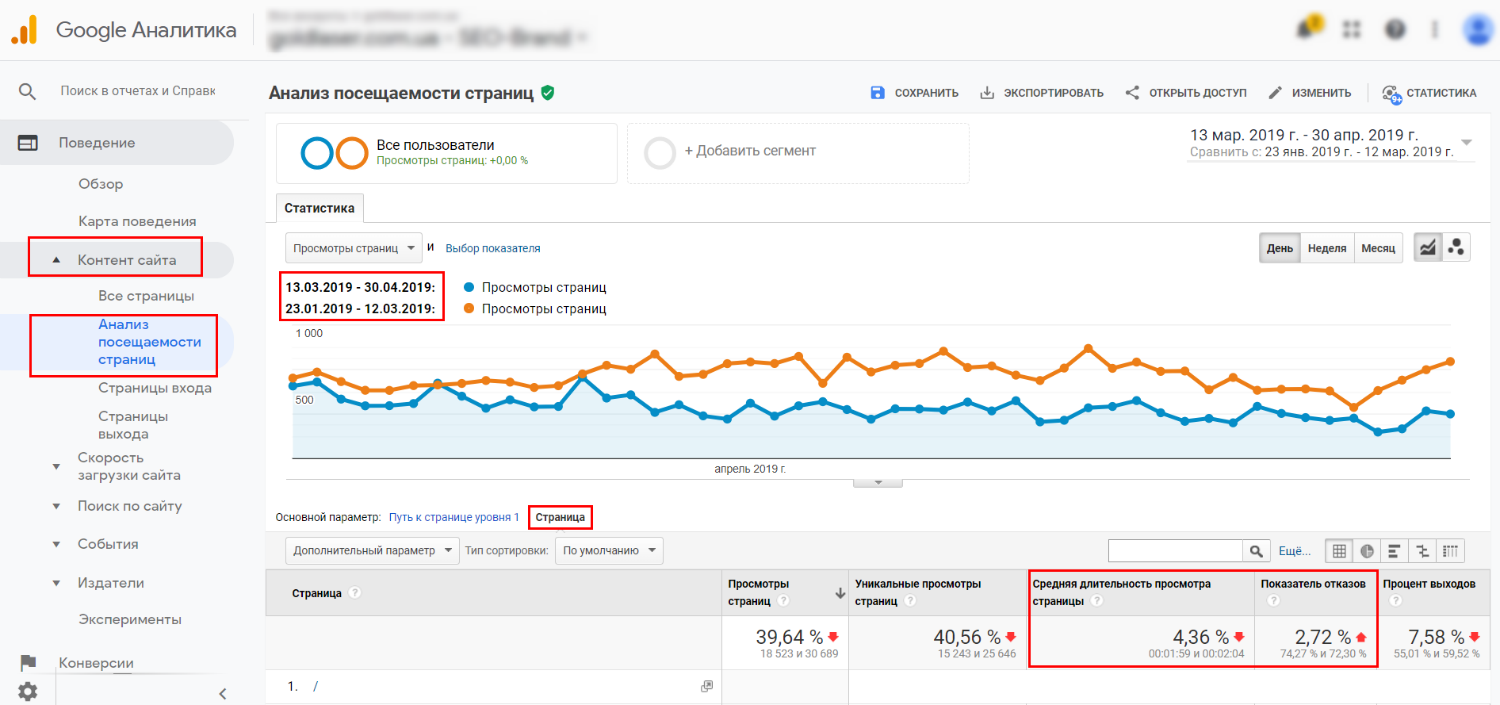
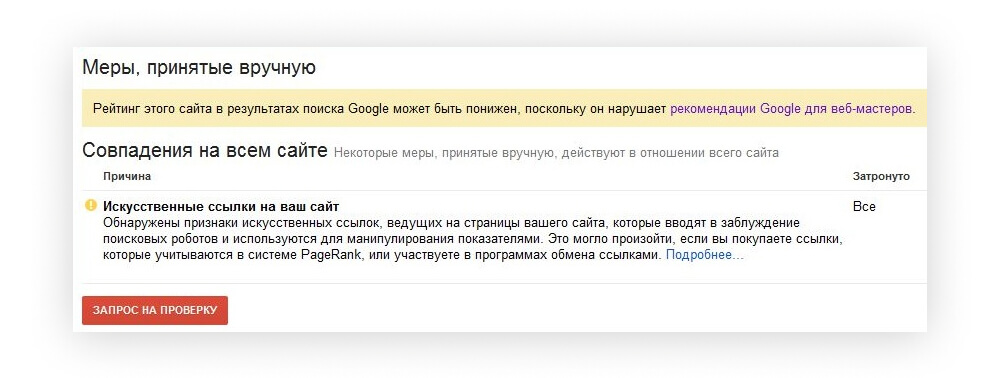

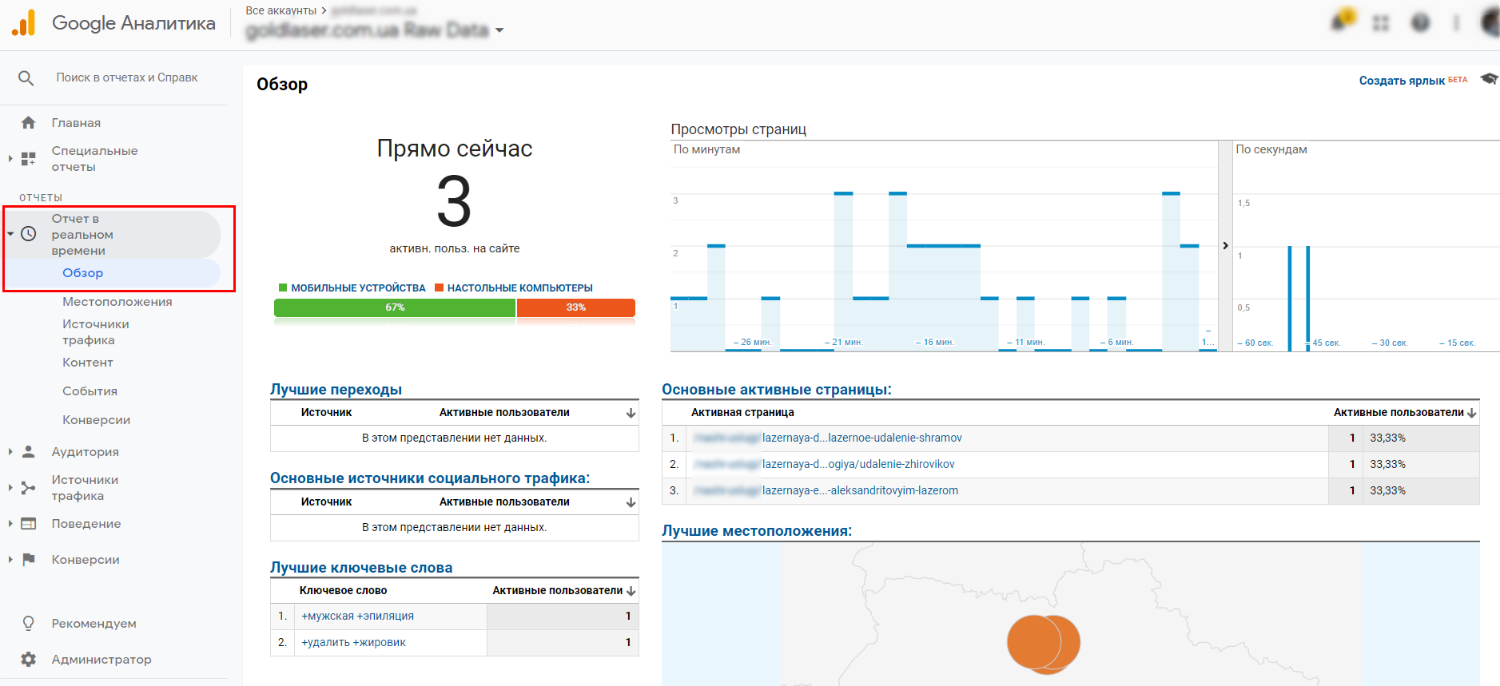


It ranks your site higher in Google, without you creating more content or building backlinks. Everything is very open with a very clear description of the challenges. It was really informative.

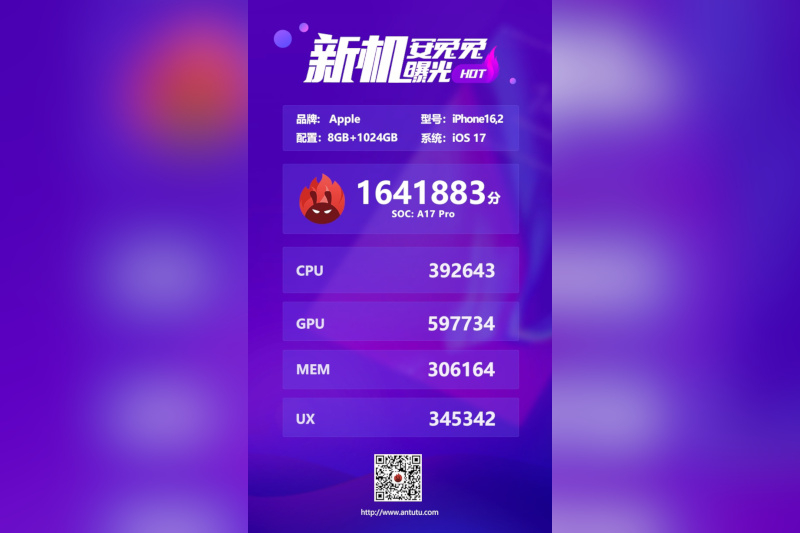
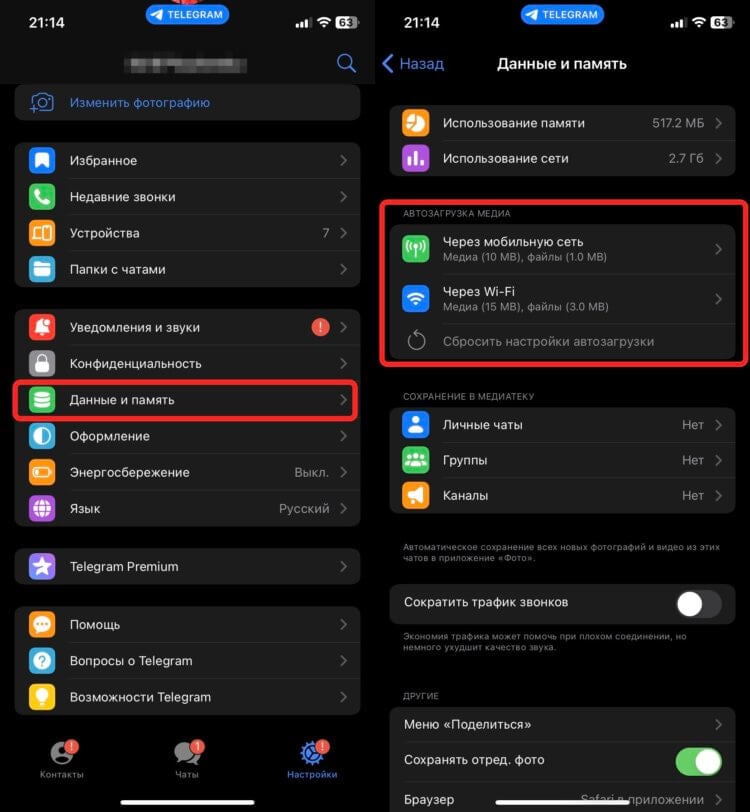
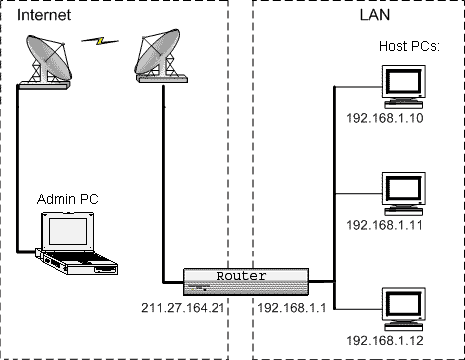
In the last post in the series on cloud computing for beginners, we analyzed the microservices features and the resources necessary for their smooth operation. In this post, we will address the issues surrounding security and encryption in cloud computing. In encryption, a key is a piece of information a parameter that determines the function of a cryptographic algorithm. It can be of two types: symmetric and asymmetric, and have several properties depending on the intended function, such as length and cryptographic period.